What exactly is fixity?
Time to explore this in detail:
File fixity, and associated digital forensics, has been a tricky technical point for me to grasp. It requires a lot of extra research as it involves different aspects and tools, but the more you look into it the more familiar it becomes.
I understood fixity and checksums better after reading this information from the DCP website. Basically, fixity demonstrates authenticity and integrity. In the preservation sense, it provides the assurance that a digital file has remained unchanged, fixed, through time.
‘Fixity doesn’t just apply to files, but to any digital object that has a series of bits inside it where that ‘bitstream’ needs to be kept intact with the knowledge that it hasn’t changed.’[1]
You can check fixity with checksums. A checksum on a file is a ‘digital fingerprint’ whereby even the smallest change to the file will cause the checksum to change completely.
Checksums are typically created using cryptographic algorithms and can be generated using various available and open source tools. Note that even though checksums can be used to establish if the contents of a file have changed, they do not tell you where in the file change has occurred.
The checksum is different from the hash value as not all hash functions are secure and the hash does not necessarily change when the data changes. A cryptographic hash function (such as SHA-1) is a checksum that is secure against malicious changes, even though in recent years their reliability has been questioned. This blog provides a useful explanation of different hash functions and some free tools to generate checksums.
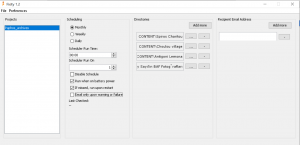
I used another checksum tool, Fixity, an open source application from AVPreserve. This is an easy tool to install and use. It can run scheduled scans and then send you emails if there is an error (see below). You can choose the checksum algorithm you prefer and filter your files.
It generates TSV file reports, creating snapshots of the manifest data of every scan and producing in this way an audit trail. According to the use guide, you can view the files in Notepad or Excel, but I only managed to view them in Notepad.
Preservation software solutions like Preservica have a built-in fixity check function (Secure Hash Algorithm, SHA-1). This commercial option offers an appealing possibility of using a holistic, out-of-the-box digital curation and preservation solution, especially when the technical skills are not there, or at least that’s what I thought. I will talk about my experiment with Preservica in my next post.
At this point I should mention a bit more about my experience with open source tools regarding digital forensics.
I tried to download and apply FTK Imager without success as I could not bypass an administrative block on my laptop. I then looked into BitCurator (also here). I started with reading some case studies to familiarise myself and Bit Curator appears as a great set of tools. According to the BitCurator Consortium, it can provide archivists new tools and methodologies to:
- Survey the extent of a collection
- Weed objects that do not fall under collecting policies
- Accession the contents of a collection
- Preserve the original order of a collection[2]
These capacities sounded very promising so after consulting the Consortium’s website and watching this YouTube video I began by downloading the BitCurator Virtual Machine 2.2.8. in order to try and test the Virtual Machine on Windows.
I installed the VirtualBox but I was not able to run BitCurator on my laptop even after extensive troubleshooting. The only explanation I can think of is that my laptop didn’t fulfil the technical requirements as it doesn’t have an i7 processor and limited memory space.
The whole process made me even more weary of DIY digital forensics and made me think that, without reliable IT support, it is perhaps safer investing on a commercial solution, especially when dealing with legal liability.
[1] “Fixity and checksums,” https://www.dpconline.org/handbook/technical-solutions-and-tools/fixity-and-checksums.
[2] “BitCurator Consortium Digital Forensics,” https://www.bitcuratorconsortium.org/digital-forensics.